

CORA-X lite is a portable applicaton to protect your sensitive data. CORA stands for context ordered replacement algorithm. CORA Cyber Security Inc empowers data security and cloud security in a manner that supersedes encryption. CORA is quantum safe (safe from all computers including quantum computers) cryptography for your data security.
CORA-X lite allows individuals, teams, businesses, offices, and organizations to secure their data.
This application uses the CORA API which can be used to protect any application, cloud or enterprise solution. The CORA API incorporates our MUPs (Multiple Use Pads) and CORA blocs to provide probabilistic encryption rather than factorization based which is one of the reasons why quantum computers will not break CORA.
The Information is presented (except in small viewing devices, such as a smartphone) along the left side of the browser and the Topics are "Affixed" to the right side of the browser.
If your viewing width is less than 768px then the Affixed Topics are hidden and the Information is presented on its own.
Thanks to jQuery and Bootstrap, these help files should be continuously readable and usable on any device or browser.
The topic, or sub-topic you are viewing will be reflected in the color and marker shown in the Affixed Topic section.
You may jump quickly to any topic by clicking/pressing on it in this Affixed Topic pane.

When you link to a particular topic, through an internal hyperlink, or the Affixed topic pane, an entry in the history chain is created and available for you to quickly move back and forth using the arrows at the bottom of the page.
In this example, the Next icon is disabled, meaning that you are at the right end of the history chain; there aren't any other topics that have been linked to after this current topic.
Quantum safe means that, no computer, including quantum computers, will break CORA's encryption.
This relys on you, the user, properly implement CORA-X with best practices; after all, the best 'safe' in the world only works 'if' you lock it, and don't leave the keys on top of the safe.
Safety, security and protection... what are these all about? Let's start with a brief analogy, think of your home. Security is like the locks on your doors and windows; it is important to secure your home. This prevents most unwanted visitors from violating your space, your home - they need your permission to enter.
Despite your best efforts, some thieves might break in without your permission. How might you protect your valuables? With a safe. Yes, this safe provides an additional level of protection, however, if the thief takes your safe home, then they have all the time in the world to crack it open.
In the digital world, this safe is better known as encryption. When standard forms of encryption lock a file, that file is essentially in a safe.
The problem here is that, if a thief takes the "safe" with the data from the server, they have all the time in the world to break it open.
Unlike a physical safe which is heavy and difficult to carry, when a computer is hacked, the digital files are light and easy to carry away.
This just isn't good enough, and that is where CORA comes in to play!
CORA is an acronym. CORA takes parts of the original file and breaks them up into different pieces (containers). More importantly, these
fragments are chosen in a context based manner so that, if someone steels one of them, they don't have enough to put "anything together".
Imagine encrypting a file, then breaking it into two pieces... this isn't context based! Each piece can provide "too much information" about the original file.
With CORA, we don't want the thieves to know anything, not even a single word from the original file!
CORA is a probabilistic encryption that relies on unfathomably large probabilities rather than complex mathematical algorithms. This makes CORA safe even when Quantum computers become a reality that breaks all other current standards of encryption.
Why CORA is unbreakable when properly implemented and used! Let us consider the main layers to CORA:
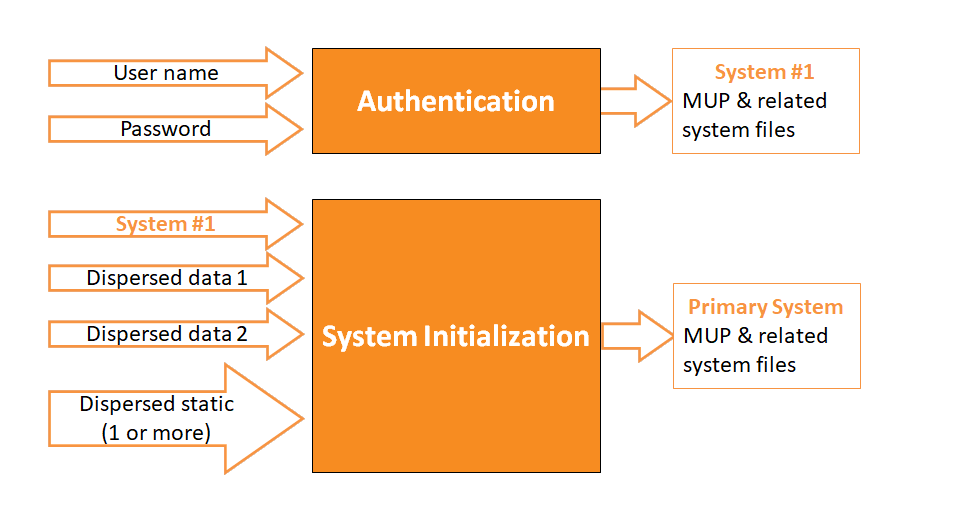
Notice above that the user must 'authenticate', then, the user must install the Encryption package which includes their MUP, which is different for every user, and at least 1 million bits long.
Why does this matter? Consider other forms of encryption, such as 1024 bit AES. This encryption always uses 1024 bits. It isn’t like yours might be 1025 bits and mine is 1031 bits. Here at CORAcsi, we don’t like giving away “any information” to a hacker or thief.
Lets talk about 1,000,000+ bit Encryption. How much stronger is a 1,000,000 bit encryption compared to a 2048? It is 10 300,413 times stronger; a number that we simply cannot relate to, however, consider that the age of our universe is approx 10 17 seconds old.
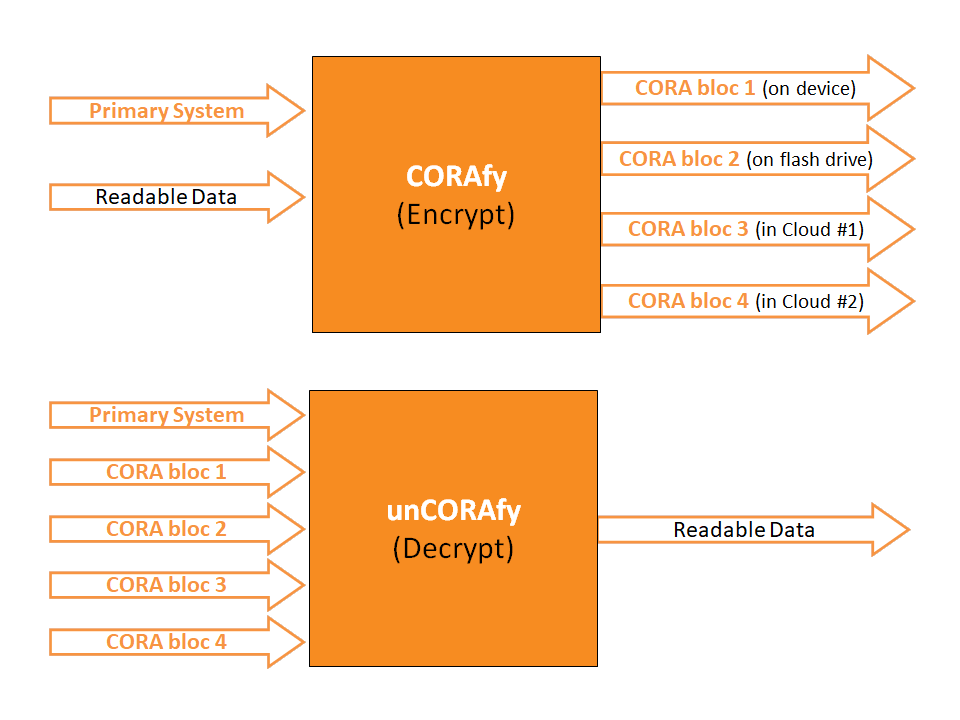
Note:
CORA-X lite is designed to have a user initialized their system once when this application is first opened so that there isn’t a risk of a thief discovering which dispersed files are used to generate the system files.
Ideally this application will run until it is time to restart the computer. The user may lock and unlock CORA-X lite as often as needed, rather than closing then opening the application which would require loading the system each time.
So you don't believe our wildly ambitious claim that CORA is quantum safe; that not even quantum computers can break CORA.
Cool, that’s great! We want you to try!
In fact, we want to host a hackathon in which we will give away a “Tesla” if you can break CORA.
Go ahead and get a head start. If you break CORA at any time, at the very least, we will provide a reward that will never be less than $1000.
It really is simple, OTP (One Time Pads) have long been identified as perfect encryption (secrecy). The only problem is that if the “same” OTP is used for two different messages, it can be broken.
CORAcsi has engineered MUPs (Multiple Use Pads) – our fancy term for OTPs that can be reused indefinitely without being broken.
Go ahead and try – use the same MUP, with CORA, on multiple messages and break it. We welcome your attempt. Let us know you are interested in breaking CORA using the online Feedback in the navigation bar above.
This happens if you haven't agreed to the End User License Agreement (EULA). Once you agree to the EULA, this diaglog should only appear if you open it, or a new EULA needs your approval.
No you do not need to use this button. If you are pleased with CORA-X lite, we would obviously appreciate your support through a donation, however, that is your free choice to make.
This link is also available for those who re interested in getting involved with CORAcsi; there are many opportunities for partnerships and joint ventures.
Cloud CORA will provide distinct advantages and will be available as a subscription. This subscription service is not yet available and that is why it is grayed out. Please stay tuned.
It is important to always backup your data. CORA is unbreakable! By its very nature, it is meant to prevent the restoring of your data unless all CORA blocs are available, "and", you have the proper System profile, including the MUP (encryption key).
This shouldn't be too surprising really. If you delete a file, and it isn't in your recycle bin, then it is gone, unless backed up.
For this reason, CORA-X lite has a backup and restore enginve for your system and user data. Additionally, there is the Backup selected data menuitem in the CORA-X Actions menu. This is meant to provide a secure backup for your actionable items to avoid this very situation in which you have CORAfied a file, and then accidentally deleted a CORA bloc.
It is highly recommended that you register your copy of CORA-X.com, however, it is optional unless you check for updates, or use the "Report Engine" to communication with CORAcsi.
There are benefits to registering with CORA-X.com, including, but not limited to:
Registering CORA-X lite does not include information about your computer hardware, software or email addresses.
CORA-X is all about probabilistic security. Hence the ticket numbers are randomized rather than sequential.
Once you have agreed to the EULA, it will not be shown by default. You may view it at any time by clicking on View EULA.
You may turn off these "overlapping" tooltips:
CORAcsi recommends using different devices for you CORA blocs. That said, you will still have the benefit of probabilistic encryption that surpasses ever other form of encryption for the following reasons:
CORA is about security; it just doesn't make sense to keep an encrption key together in one place.
Smart, motivated hackers often know where to look, or what to look for.
They have often found the encryption keys and used them to decrypt the protected data.
Back when computers where first on the market, memory was expensive and hard to come by. "Back then" it made sense to have shorter keys while making use of complicated mathematical transformations.
Today memory is cheap and readily available. This is true for computers, and well as ASIC chips used for autonomous and connected vehicles, and all IoT devices.
More importantly, Claude Shannon long ago identified One Time Pads as perfect encryption (secrecy). In other words, having longer keys is by far more secure, if only they could be practical and reusable. CORA is practicle and reusable. Probabalisitic is far more secure!
Finally, a million bit key is only 125 kB, and with dispersed files, only part of that needs to be on a smaller IoT device.
CloudCORA.com will provide a subscription service for CORA enabled applications.