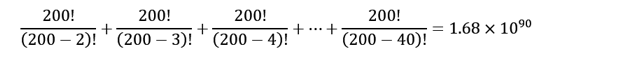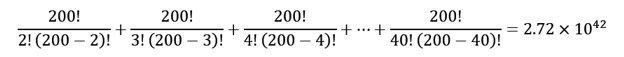CORA Cyber Security Inc. brings you quantum safe cryptography using a minimum of 125 kB Multiple Use Pad (MUP), resulting in data security that is quantum-safe today and tomorrow.
The CORA API
CORA-X uses the CORA API to handle the security. All of these features are available through the CORA API.
Why is CORA so great?
- CORA is probabilistic rather than factorization based (disregard Shor & Grover's algorithms).
- The probabilities involved are too large for any computer to break. Our 1,000,000+ bit encyrption is 10 300,413 times stronger than 2048 bit encryption.
-
CORA blocs are distributed through out the device, and ideally, onto different devices and clouds. Take a moment to think about what this means?
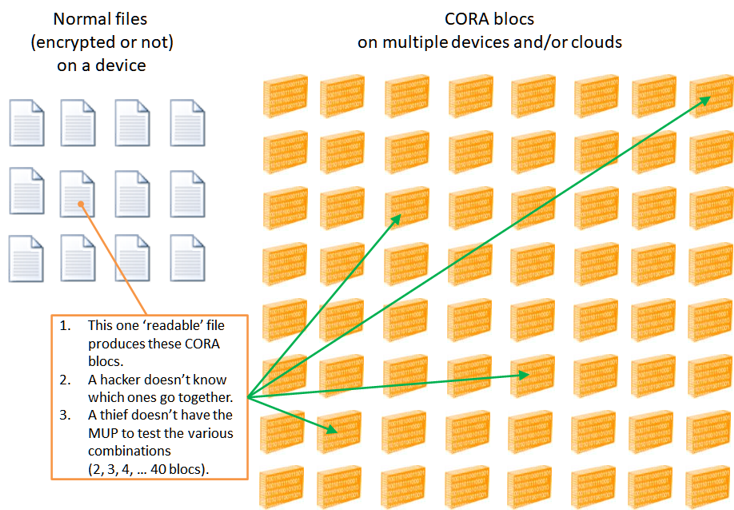
- Every single file that is CORAfied (encrypted) results in 2 - 40 CORA blocs.
- How would an attacker know how many or which CORA blocs go together?
- A thief would have to try every permutation and that is only possible if they have the MUP (huge Encryption key) which they should never obtain.
-
If just 100 files are CORAfied, then that would result in between 200 and 4000 CORA blocs (if previous CORA blocs had been deleted, rather than accumulate).
Consider just 200 CORA blocs:
-
Total number of permutations required to test 2-40 CORA blocs:
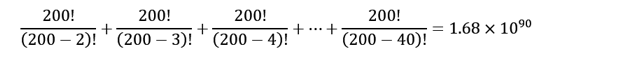
-
Let's say we make it a bit easier and don't require that the CORA blocs be entered in the proper order (nah), then the total number of combinations to test
2-40 CORA blocs is only:
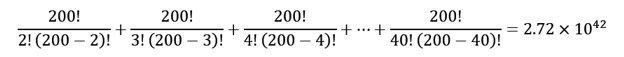
That's right, 1042 - unimaginable, and that's with only 200 CORA blocs.
- If a single byte in the MUP or CORA blocs is corrupt, then the solution fails to decrypt. Hence ransomware that has infected CORAfied data will not propagate.
Self-healing
Enterprise level solutions have the opportunity to implement CORA as a
Self Healing security platform.
Do your due diligence and monitor access to the CORA blocs.
If a single CORA bloc is 'possibly' compromised in your data centre, or on one of your Cloud based external servers, then delete any single CORA bloc
and generate a new solution. The new CORA blocs are independant of the original CORA blocs. The comprimised CORA bloc(s) are useless (and don't forget, all of the CORA blocs without the MUP are in fact useless).
Imagine
If a hacker breaches your server, you may confidently announce to the global community that the breach resulted in "zero" readable files, passwords or client records being "read".
Now that makes for a great Public Relations announcement.
Better yet, a properly constructed self-healing implementation should have your registered users, employees or clients up an running, securely, minutes after a breach occurs.