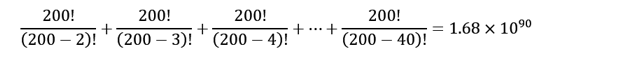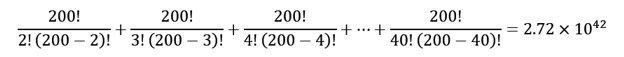CORA-X lite for Teams uses Subscription based dispersed files to provide a smooth, user friendly and secure means of providing 'targeted' encryption that traditional and quantum computers cannot break.
CORA-X uses the CORA API to handle the security. All of these features are available through the CORA API.
Why is CORA-X for teams so great?
- CORA is probabilistic rather than factorization based (disregard Shor & Grover's algorithms).
- The probabilities involved are too large for any computer to break. Our 1,000,000+ bit encyrption is 10 300,413 times stronger than 2048 bit encryption.
-
CORA blocs are distributed through out the device, and ideally, onto different devices and clouds. Take a moment to think about what this means?
Read more »
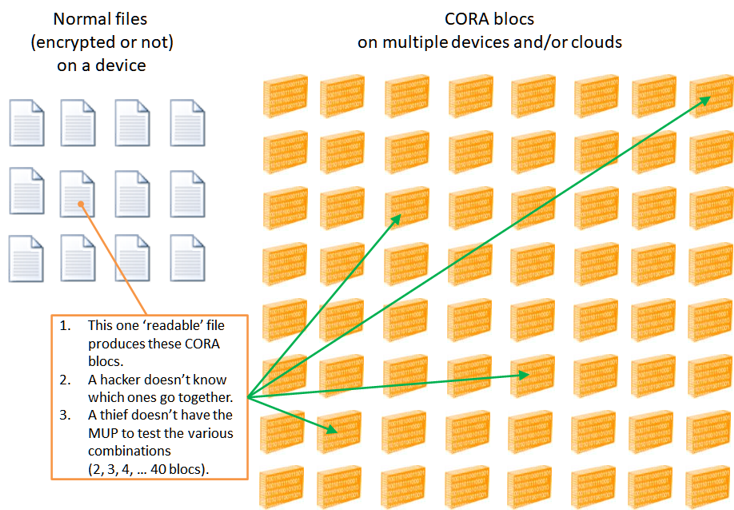
- Every single file that is CORAfied (encrypted) results in 2 - 40 CORA blocs.
- How would an attacker know how many or which CORA blocs go together?
- A thief would have to try every permutation and that is only possible if they have the MUP (huge Encryption key) which they should never obtain.
-
If just 100 files are CORAfied, then that would result in between 200 and 4000 CORA blocs (if previous CORA blocs had been deleted, rather than accumulate).
Consider just 200 CORA blocs:
-
Total number of permutations required to test 2-40 CORA blocs:
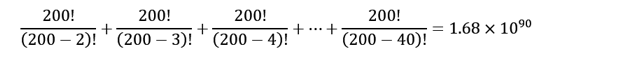
-
Let's say we make it a bit easier and don't require that the CORA blocs be entered in the proper order (nah), then the total number of combinations to test
2-40 CORA blocs is only:
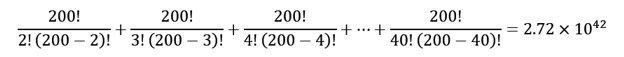
That's right, 1042 - unimaginable, and that's with only 200 CORA blocs.
- If a single byte in the MUP or CORA blocs is corrupt, then the solution fails to decrypt. Hence ransomware that has infected CORAfied data will not propagate.
-
Depending on your organizations needs, CORA may be implemented as 'Self-healing'; if a breach occurs on one computer, any single bloc is then deleted from a Cloud based location, then another solution is created in moments. Proudly announce to stakeholders that a breach occurred and yet, not a single readable file will be violated and your service was up again in minutes.
- Individuals may belong to multiple teams. Easily switch back and forth using the Profile Manager. Each Profile (team) will automatically load their unique System (Encryption key) and associated Actionable items (files/folders).
Get your quote today using the Contact action in the navigation bar.